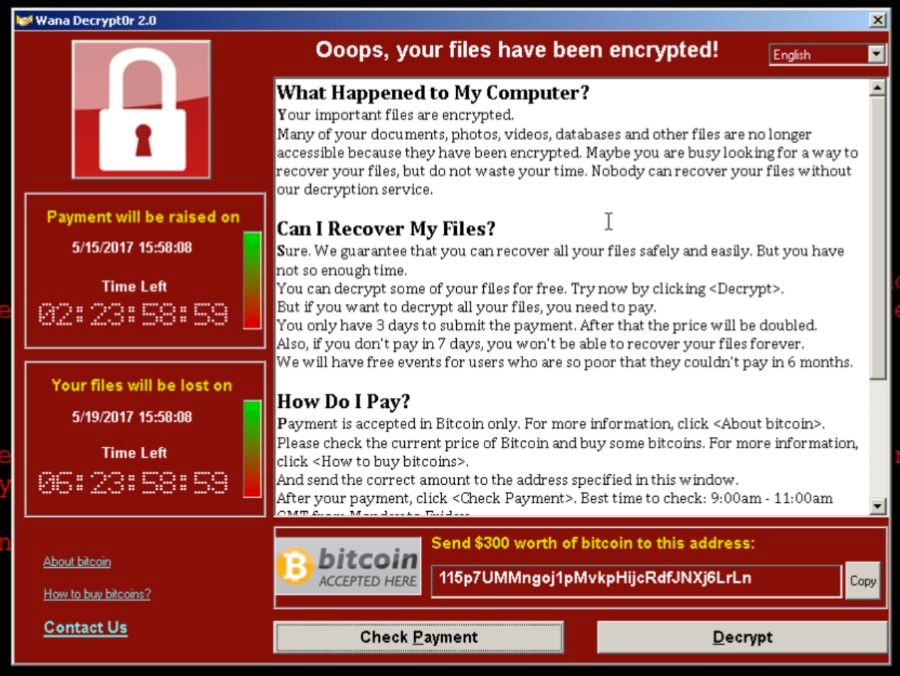
Don’t let this happen to you! Take steps to guard against ransomware!
PC and servers around the world are currently under attack by a new super-malware called WannaCrypt. It is a highly infectious drive-by ransomware attack, and WannaCrypt Ransomware is spreading “like wildfire” in Europe and other parts of the world. 73 countries have reported attacks this month, May, 2017.
Here is what you need to know about WannaCrypt:
All Windows systems are impacted by a vulnerability in the Windows Server Message Block protocol. WannaCrypt uses an exploit called EternalBlue to infect new PCs without user action.
To protect your system from this exploit, make sure you have applied all available updates and patches available through Windows Update. For more information consult this Microsoft Security Bulletin and this Microsoft Customer Guidance for WannaCrypt Attacks.
Microsoft has provided users of Windows XP access to the necessary patches. Check this Microsoft Update Catalog site.
Made in the USA
The WannaCrypt story is disconcerting because it uses a recently-compromised American cyberweapon called EternalBlue. EternalBlue came from the National Security Agency (NSA) at Fort Meade, MD. EternalBlue was apparently stolen from the NSA and released onto the Internet by the Shadow Brokers hacker group on April 14, 2017.
EternalBlue uses a “divide and conquer” strategy that is used with large teams of engineers and scientists working together to build new applications. There could be hundreds or even thousands of people working on parts of projects like EternalBlue.
By using secret flaws in SMBv1, EternalBlue gives NSA agents the ability to write custom software to penetrate a target’s Windows PC and perform surreptitious data collection and system modification, all with zero user awareness. This is what I call a “drive-by” or “sneak-and-peak” attack capability, which is much more insidious than a phishing email which requires user activation.
For comparison, look at an older ransomware villain like CryptoLocker, that depends on the user clicking on a link or activating executable code to start the attack.
WannaCrypt is something else entirely. Powered-up with military-grade American cyberweapons, WannaCrypt is a monstrously dangerous new class of malware that is distributed automatically to any Windows computer connected to a network.
Act Now – Eliminate the EternalBlue Vulnerability
This is an IT Red Alert. The NSA is compromised, and there is drive-by ransomware in the wild.
Microsoft is working hard to eliminate the flaw. All the details are at Microsoft Security Bulletin MS17-010: Security Update for Microsoft Windows SMB Server.
Hopefully you have been keeping up with your Windows updates, and you have ditched Windows XP long ago. Microsoft distributed the EternalBlue SMB Server patch in the March 2017 Microsoft rollup patches.
But, there are literally hundreds of millions of Internet-connected PC’s out in the wild that don’t get the care and feeding they need. Apparently, there are WannaCrypt infections in infrastructure elements in Britain’s National Health Service (NHS) and Telefonica’s telecom operations. Per this Wired article, WannaCrypt is spreading like wildfire and has been reported in 73 countries.
Yes, It is Time to Worry!
This powerful creature from Ridley Scott’s Promethus is a hybrid of the famous Alien and the superhuman Engineers. This is like the monster that been created by combining EternalBlue with ransomware
WannaCrypt is a significant malware development and it deserves our fear and respect. WannaCrypt itself is a mutant child like the Alien/Engineer mashup from Ridley Scott’s movie Prometheus. Mashing up ransomware with Military-Grade penetration software has created WannaCrypt, a monstrous new threat.
There are dozens if not hundreds of still-secret zero-days in the hands of various actors. Zero-day actors range from individuals, criminal gangs, the IT industry, and nation-states flexing their military and intelligence-gathering resources.
Another disturbing trend is the packaging of cyberweapons into online services you can buy. If you have enough bitcoin, then there is a Cyber-arms Industry where you can find middlemen who will sell you a zero-day exploit. It will cost you, though. Prices for zero-day exploits are estimated to be from $10,000 to $100,000 and up. Someday soon, you’ll be able to go on the dark web and “own” a target’s cyberlife using Zero-Days-as-a-Service (ZDaaS) for just a few bitcoins.
What to Do Now?
It seems like a major threshold has been crossed with the NSA being compromised and military-grade cyberweapons are being mashed up with lucrative criminal schemes like ransomware.
This needs discussion at the national and international level. The public needs to become aware of the failure of the NSA to keep a dangerous tool like EternalBlue safeguarded and how the US Government is actually responsible for weaponizing one of the most dangerous parts of the Internet.
There needs to be a more scientific and common-sense approach to having secure communications and what it means to have privacy in the 21st century. Law enforcement agencies need new tools, laws, procedures and mandates for putting cybercriminals out of business. There will be challenges keeping stepped up law enforcement compatible with the freedom of speech and universal access which drives the growth of the Internet.
Clearly, there are major computer science challenges inherent in making our hardware platforms, communication networks and operating systems more secure. The best direction I’ve seen for security is the walled-garden approach. In a walled garden OS like the iPhone, every single app must be certified and they have very restricted inter-application communication capabilities. As far as the other few billion computers and devices already out there, due to historical realities, I fear we may never figure out how to eliminate new zero-days on Windows, MacOS and Linux.
In the short term, I am concerned that another new zero-day exploit like WannaCrypt will pop up and have a more widespread impact in the US. If it is serious enough, such an attack could trigger an official response on the part of US Cyber Command. Just think of the unanticipated consequences of the US going public with our cyberweapon capabilities.
Here Is How To Stay Calm
As a business owner, what are you to do in these situations? The only good advice to to have a strong security policy and review that policy at least once a year.
I go over many of the basic threats and defensive strategies in my April 22, 2016 post on Top 4 Security Threats for Business Owners in 2016.
- Top 4 Security Threats for Business Owners
- Social Engineering, which is a polite term for lying bast**ds. Please keep an eye out for those lying bast**ds and think twice when you get an email from the boss asking to send a wire transfer or a phone call from someone frantic to get a password on a user account.
- Spear Phishing is a technological attack where clicking on a lure will activate code that infects your desktop computer with a keylogger. Then, the attacker will sit back and wait for you to log onto a bank account, or for a system administrator to enter a root password to a server system.
- Ransomware is attack malware that will encrypt your servers with an unbreakable key and demand a bitcoin ransom for the key. Ransomware payloads are frequently delivered via Spear Phishing links. WannaCry uses a “drive by” infection technique, so that’s what makes it so treacherous and onerous.
- Botnets are international networks of millions of computers and Internet-connected devices infected with “zombie” malware. Each botnet has a commander who can deploy distributed denial of service (DDoS) attacks and other offensive cyberweapons.
- In the April 2016 blog post, I walk you through the things you need to do to protect yourself.
- Be more proactive and professional in your enterprise network management.
- Minimize all Attack Surfaces where bad actors will test your defenses.
- Keep your patches up to date to avoid Zero-Day Exploits, which are newly-discovered flaws in existing operating systems like Windows.
- Use PC and file server scanners and real-time malware protection tools. That means going with a Windows malware product like BitDefender Advanced Security. If you are running in a pure Windows 10 and Server 2016 environment, using Windows Defender is good security practice and an alternative to buying a product like BitDefender.
- Use an online or cloud-based backup system to store multiple versions of your server files offsite. In case of a ransomware attack, you’ve got protected copies of your business data.
Telnexus Can Help
If you want a security review, are dealing with a security problem, want to make sure your PCI network is compliant, or if your medical office is HIPAA-compliant, then Telnexus can help. We start with a free telephone consultation and can followup with network redesigns, new security appliances, written documentation and best practices.
Give Telnexus a call today at (510) 859-7000 or email us at info@telnexus.com to start a security conversation.